A friend put his corporate website on his cloud host, and the traffic was not large. However, because it was used and was often attacked by CC, the main manifestation was that the IO and CPU increased sharply. Finally, the database hung up and the website became inaccessible. Cloudflare was enabled at the beginning, but the attacker scanned frantically and the defense effect was average.
In order to accurately identify malicious IPs, you need to enable the Real IP module in Nginx and Apache after enabling Cloudflare CDN, then use scripts to analyze website logs, collect abnormal IPs from the logs, and then use the Cloudflare API to add malicious IPs to Cloudflare in batches in the firewall.
Of course, when the website encounters very powerful CC and DDoS attacks, we can enable Cloudflare's classic 5-second shield to prevent attacks. If we cannot grasp the frequency of attacks, we can set up a scheduled task. When the system load exceeds a certain value (generally The attack will cause the system load to explode), call the Cloudflare API to enable the 5-second shield.

For more on website security and optimization, here are:
- Five security tips for using a free VPS control panel – don’t let hackers take advantage
- Linux php-fpm optimization experience-php-fpm process takes up large memory and does not release memory problems
- Enable HSTS and join the HSTS Preload List to make HTTPS access to the website more secure - with a method to delete HSTS
PS: Updated on March 25, 2019, Regarding the security issues of VPS, many friends may ignore the SSH configuration of the VPS itself. Here are the strengthening strategies: VPS host and server security protection: SSH modification port, add Whitelist, key login only.
PS: Updated on January 4, 2020, Cloudflare Railgun is the ultimate acceleration solution provided by Cloudflare specifically for Business and Enterprise customers. However, it can be turned on for free through Cloudflare Partner: Turn on Cloudflare Railgun acceleration for free - reduce connection delays and achieve dynamic page caching and acceleration.
1. Cloudflare automatically blocks malicious IPs
1.1 Find the malicious IP
Use a script to analyze the frequency of access to a single IP in one minute. If the frequency exceeds a certain frequency (generally, normal access should not exceed 60 times in one minute, you can set it to a smaller value), it is considered a malicious IP. The script is as follows:
#/bin/bash
#日志文件,你需要改成你自己的路径
logfile=/data/wwwlogs/
last_minutes=1
#开始时间1分钟之前(这里可以修改,如果要几分钟之内攻击次数多少次,这里可以自定义)
start_time= date +"%Y-%m-%d %H:%M:%S" -d '-1 minutes'
echo $start_time
#结束时间现在
stop_time=`date +"%Y-%m-%d %H:%M:%S"`
echo $stop_time
cur_date="`date +%Y-%m-%d`"
echo $cur_date
#过滤出单位之间内的日志并统计最高ip数,请替换为你的日志路径
tac $logfile/sky.ucblog.net_nginx.log | awk -v st="$start_time" -v et="$stop_time" '{t=substr($2,RSTART+14,21);if(t>=st && t<=et) {print $0}}' | awk '{print $1}' | sort | uniq -c | sort -nr > $logfile/log_ip_top10
ip_top=`cat $logfile/log_ip_top10 | head -1 | awk '{print $1}'`
ip=`cat $logfile/log_ip_top10 | awk '{if($1>2)print $2}'`
# 单位时间[1分钟]内单ip访问次数超过2次的ip记录入black.txt,这里wzfou.com为了测试设置了2,你需要改成其它的数字
for line in $ip
do
echo $line >> $logfile/black.txt
echo $line
# 这里还可以执行CF的API来提交数据到CF防火墙
done1.2 Add IPs to the firewall in batches
Use the following code to add malicious IPs to Cloudflare's firewall in batches. Remember to replace it with your Cloudflare API.
#!/bin/bash
# Author: Zhys
# Date : 2018
# 填Cloudflare Email邮箱
CFEMAIL="freehao123@gmail.com"
# 填Cloudflare API key
CFAPIKEY="xxxxxxxxxxxxxxxx"
# 填Cloudflare Zones ID 域名对应的ID
ZONESID="xxxxxxxxxxxxxxxxxxxx"
# /data/wwwlogs/black.txt存放恶意攻击的IP列表
# IP一行一个。
IPADDR=$(</data/wwwlogs/black.txt)
# 循环提交 IPs 到 Cloudflare 防火墙黑名单
# 模式(mode)有 block, challenge, whitelist, js_challenge
for IPADDR in ${IPADDR[@]}; do
echo $IPADDR
curl -s -X POST "https://api.cloudflare.com/client/v4/zones/$ZONESID/firewall/access_rules/rules"
-H "X-Auth-Email: $CFEMAIL"
-H "X-Auth-Key: $CFAPIKEY"
-H "Content-Type: application/json"
--data '{"mode":"block","configuration":{"target":"ip","value":"'$IPADDR'"},"notes":"CC Attatch"}'
done
# 删除 IPs 文件收拾干净
rm -rf /data/wwwlogs/black.txt1.3 Automatically find malicious IPs and add them to the firewall
Just merge the above two scripts into one script.
#/bin/bash
#日志文件,你需要改成你自己的路径
logfile=/data/wwwlogs/
last_minutes=1
#开始时间1分钟之前(这里可以修改,如果要几分钟之内攻击次数多少次,这里可以自定义)
start_time= date +"%Y-%m-%d %H:%M:%S" -d '-1 minutes'
echo $start_time
#结束时间现在
stop_time=`date +"%Y-%m-%d %H:%M:%S"`
echo $stop_time
cur_date="`date +%Y-%m-%d`"
echo $cur_date
#过滤出单位之间内的日志并统计最高ip数,请替换为你的日志路径
tac $logfile/sky.ucblog.net_nginx.log | awk -v st="$start_time" -v et="$stop_time" '{t=substr($2,RSTART+14,21);if(t>=st && t<=et) {print $0}}' | awk '{print $1}' | sort | uniq -c | sort -nr > $logfile/log_ip_top10
ip_top=`cat $logfile/log_ip_top10 | head -1 | awk '{print $1}'`
ip=`cat $logfile/log_ip_top10 | awk '{if($1>2)print $2}'`
# 单位时间[1分钟]内单ip访问次数超过2次的ip记录入black.log,这里为了测试设置2,你需要改成其它的数字
for line in $ip
do
echo $line >> $logfile/black.txt
echo $line
# 这里还可以执行CF的API来提交数据到CF防火墙
done
# 填Cloudflare Email邮箱
CFEMAIL="freehao123@gmail.com"
# 填Cloudflare API key
CFAPIKEY="xxxxxxxxxxxxxxxxxxxxxxxx"
# 填Cloudflare Zones ID 域名对应的ID
ZONESID="xxxxxxxxxxxxxxxxxxxxxxxxxxx"
# /data/wwwlogs/black.txt存放恶意攻击的IP列表
# IP一行一个。
IPADDR=$(</data/wwwlogs/black.txt)
# 循环提交 IPs 到 Cloudflare 防火墙黑名单
# 模式(mode)有 block, challenge, whitelist, js_challenge
for IPADDR in ${IPADDR[@]}; do
echo $IPADDR
curl -s -X POST "https://api.cloudflare.com/client/v4/zones/$ZONESID/firewall/access_rules/rules"
-H "X-Auth-Email: $CFEMAIL"
-H "X-Auth-Key: $CFAPIKEY"
-H "Content-Type: application/json"
--data '{"mode":"block","configuration":{"target":"ip","value":"'$IPADDR'"},"notes":"CC Attatch"}'
done
# 删除 IPs 文件收拾干净
rm -rf /data/wwwlogs/black.txtI have put the above script in my download center and can provide it for everyone to download and use. The code is as follows:
wget https://do.wzfou.net/shell/attack-ip.sh chmod +x /qicmd/cfblockip.sh ./cfblockip.sh wget https://do.wzfou.net/shell/attack-ip.sh chmod +x /qicmd/attack-ip.sh ./attack-ip.sh wget https://do.wzfou.net/shell/cf-block-attack-ip.sh chmod +x /qicmd/cf-block-attack-ip.sh ./cf-block-attack-ip.sh
Finally, set a scheduled task and let the script detect it every minute (please adjust it as needed. For the use of scheduled tasks, refer to: Linux Crontab command scheduled task basic syntax)
* * * * * /bin/bash /root/cf-block-attack-ip.sh > /tmp/ou1t.log 2>&1
The effect of automatically adding malicious IPs to CloudFlare firewall is as follows:

2. Cloudflare automatically switches 5-second shield script
website:
- HTTPS://GitHub.com/MAPUMP/cloud flare-block
When your server is under attack, the system load will explode. Use a script to automatically detect the system load. When the pressure exceeds a certain value, you can switch to "I'm Under Attack!" mode. The steps are as follows:
#下载 cd /root && git clone https://github.com/Machou/Cloudflare-Block.git DDoS #打开Cloudflare.sh,修改配置 API_KEY You're Global API Key (https://dash.cloudflare.com/profile) MAIL_ACCOUNT Email of your Cloudflare account DOMAIN Zone ID (https://dash.cloudflare.com/_zone-id_/domain.com) #设置定时任务 crontab -e */1 * * * * /root/DDoS/Cloudflare.sh 0 # check every 1 minute if protection is not enabled */20 * * * * /root/DDoS/Cloudflare.sh 1 # check every 20 minutes if protection is enabled
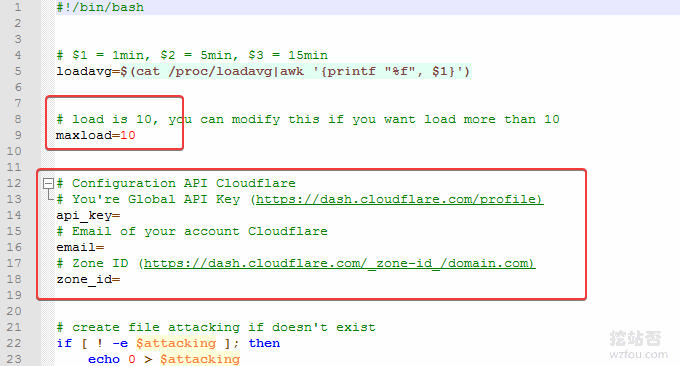
By default, the script detects system load at 10 and activates “I’m Under Attack!” mode. You can adjust this as needed. As shown below:
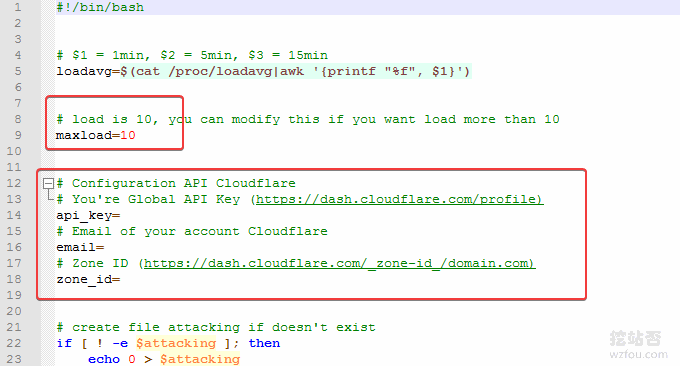
The complete script code is as follows:
#!/bin/bash
# $1 = 1min, $2 = 5min, $3 = 15min
loadavg=$(cat /proc/loadavg|awk '{printf "%f", $1}')
# load is 10, you can modify this if you want load more than 10
maxload=10
# Configuration API Cloudflare
# You're Global API Key (https://dash.cloudflare.com/profile)
api_key=
# Email of your account Cloudflare
email=
# Zone ID (https://dash.cloudflare.com/_zone-id_/domain.com)
zone_id=
# create file attacking if doesn't exist
if [ ! -e $attacking ]; then
echo 0 > $attacking
fi
attacking=./attacking
hasattack=$(cat $attacking)
if [ $(echo "$loadavg > $maxload"|bc) -eq 1 ]; then
if [[ $hasattack = 0 && $1 = 0 ]]; then
# Active protection
echo 1 > $attacking
curl -s -X PATCH "https://api.cloudflare.com/client/v4/zones/$zone_id/settings/security_level"
-H "X-Auth-Email: $email"
-H "X-Auth-Key: $api_key"
-H "Content-Type: application/json"
--data '{"value":"under_attack"}'
fi
else
if [[ $hasattack = 1 && $1 = 1 ]]; then
# Disable Protection
echo 0 > $attacking
curl -s -X PATCH "https://api.cloudflare.com/client/v4/zones/$zone_id/settings/security_level"
-H "X-Auth-Email: $email"
-H "X-Auth-Key: $api_key"
-H "Content-Type: application/json"
--data '{"value":"high"}'
fi
fi
exit 0
3. Summary
Cloudflare is a very easy-to-use tool to defend against DDos and CC attacks. The free version of Cloudflare combined with the API can achieve more flexible functions and is sufficient for ordinary defense.
Cloudflare protection also has certain problems, that is, after enabling Cloudflare, the IP of the user obtained is the IP of the Cloudflare CDN node. We also need to do further optimization in the server configuration.
