Before buying a VPS host, I usually check the reviews of other people using the VPS host. In particular, the line of the VPS host is what I am most concerned about. Because there are many foreign VPS hosting providers, but there are only a few computer rooms with fast access speeds from China. A VPS with poor lines and slow speed is not suitable for building a Chinese website.
At the same time, I also discovered another problem, that is, the line quality of a certain VPS host was very good during the initial test, but as the number of users increased, access to the VPS host became more and more unstable. This was the first time I used the VPS host. Not expected. Therefore, there is an urgent need for a foreign VPS host line monitoring report to intuitively understand the changes in the VPS host line.
Smokeping is probably the only one that meets the above requirements. Smokeping is an open source and free network performance monitoring tool. It is mainly used to monitor network performance, including conventional ping, dig, echoing, curl, etc. It can monitor www server performance, monitor dns query performance, monitor s-s-h performance, etc. The most important thing is that Smokeping's charts are very intuitive.
Smokeping uses rrdtool as support. The generated network delay data conversion chart is very beautiful and supports interactive graphical browsing. You can view monitoring data for any period of time. Smokeping can also deploy master/slave distributed measurement, that is, use one server as the "master", and other servers as "slave" and transmit data to the "master" server, and finally summarize it to form a system monitoring data chart.

This article will share the installation and configuration methods of Smokeping. For more information on VPS host performance and speed evaluation, please refer to: VPS host ranking list. You can also conduct a "physical examination" of the VPS host by yourself according to the following method:
- Summary of VPS hosting providers and computer rooms connected to CN2 lines - reference manual for identifying genuine and fake CN2 line hosts
- Three free tools to help you detect the authenticity of VPS servers - VPS host performance and speed test methods
- A webmaster who has used Alibaba Cloud VPS hosting for three years summed up the five major characteristics of Alibaba Cloud
PS: Updated on October 21, 2017, If you find that your VPS server is often down or abnormal, you may be able to use this tool to find out the "real culprit": server log analysis tool: ngxtop and GoAccess - real-time monitoring and visual management to quickly find the source of anomalies.
PS: Updated on October 27, 2018, Manual installation of Smokeping is troublesome. Interested friends can try the SmokePing Nginx one-click installation package: Network monitoring tool: SmokePing Nginx one-click installation/management script.
1. Preparation before installation of Smokeping
Smokeping official website:
- HTTPS://OSS.Oh eh for guests.EAT/samokelping/index.EN.HTML
- HTTPS://GitHub.com/Oheh for guests/smoke ping
Smokeping requires the following component dependencies (optional is optional):
RRDtool 1.2.x or later
FPing (optional)
EchoPing (Optional)
Curl (Optional)
dig (Optional)
S-S-H (Optional)
Webserver
Perl 5.8.8 or later (the corresponding modules are as follows)
FCGI
CGI, CGI::Fast
Config::Grammar
LWP
Socket6 (optional)
Net::Telnet (optional)
Net::OpenS-S-H (optional)
Net::.DNS (optional)
Net::LDAP (optional)
IO::Socket::SSL (optional)
Authentic::Radius (optional)
The Smokeping official website recommends running it with Apache. Of course, you can also use Nginx, but you need to configure Nginx FCGI. The environment tested in this article is: CentOS 6.8+Apache. Execute the following commands to install related component dependencies:
#临时修改hostname
sudo hostname ping.wzfou.com
#查看是否成功
hostname
#永久修改Hostname
vi /etc/sysconfig/network
#修改原hostname为
ping.wzfou.com
#查看是否成功
hostname
//如果是CentOS 7,永久性的修改主机名称,重启后能保持修改后的。
hostnamectl set-hostname ping.wzfou.com
//重启后可以看到
hostnamectl
#禁用SELinux
vi /etc/selinux/config
SELINUX = disabled
#同步时间
yum -y install ntpdate
ntpdate times.aliyun.com
#安装epel源
wget http://download.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
rpm -ivh epel-release-6-8.noarch.rpm
#备用地址:https://do.wzfou.net/wzfou/epel-release-6-8.noarch.rpm
#安装rrdtool与依赖库
yum -y install perl perl-Net-Telnet perl-Net-DNS perl-LDAP perl-libwww-perl perl-RadiusPerl perl-IO-Socket-SSL perl-Socket6 perl-CGI-SpeedyCGI perl-FCGI perl-CGI-SpeedCGI perl-Time-HiRes perl-ExtUtils-MakeMaker perl-RRD-Simple rrdtool rrdtool-perl curl fping echoping httpd httpd-devel gcc make wget libxml2-devel libpng-devel glib pango pango-devel freetype freetype-devel fontconfig cairo cairo-devel libart_lgpl libart_lgpl-devel mod_fastcgi mod_ssl git bind-utils fping
#安装中文字体
yum -y install wqy-zenhei-fonts #DNS需要用到TCPPing命令,安装方法如下: 首先安装tcptraceroute: yum install tcptraceroute 然后下载: wget http://www.vdberg.org/~richard/tcpping 赋予权限后移动到/usr/bin目录下即可使用: chmod 755 tcpping mv tcpping /usr/bin/ 经过测试,发现tcpping的IP必须要有80服务才行During the installation process, a certain dependency may not be found. Generally, the impact is not significant. You only need to be able to perform the following operations normally.

2. Download Smokeping, install and configure it
Execute the following command to start installing Smokeping:
wget http://oss.oetiker.ch/smokeping/pub/smokeping-2.6.9.tar.gz
tar zxvf smokeping-2.6.9.tar.gz
cd smokeping-2.6.9
./configure --prefix=/usr/local/smokeping
./setup/build-perl-modules.sh /usr/local/smokeping/thirdparty
#备用地址:https://do.wzfou.net/wzfou/smokeping-2.6.9.tar.gz
安装过程中,可能会出现下面的提示:
** Aborting Configure ******************************
If you know where perl can find the missing modules, set
the PERL5LIB environment variable accordingly.
FIRST though, make sure that 'perl' starts the perl
binary you want to use for SmokePing.
Now you can install local copies of the missing modules
by running
./setup/build-perl-modules.sh /usr/local/smokeping/thirdparty
The RRDs perl module is part of RRDtool. Either use the rrdtool
package provided by your OS or install rrdtool from source.
If you install from source, the RRDs module is located
PREFIX/lib/perl
#这是因为缺少相应的perl模块,直接按照提示执行:
./setup/build-perl-modules.sh /usr/local/smokeping/thirdparty
#继续执行操作:
./configure --prefix=/usr/local/smokeping
/usr/bin/gmake installExecute the following command to start configuring Smokeping:
#创建 cache、data、var 数据目录
cd /usr/local/smokeping
mkdir cache data var
#创建日志
touch /var/log/smokeping.log
#授权
chown apache:apache cache data var
chown apache:apache /var/log/smokeping.log
#修改配置文件
cd /usr/local/smokeping/htdocs/
mv smokeping.fcgi.dist smokeping.fcgi
cd /usr/local/smokeping/etc
mv config.dist config
#vim config
#cgiurl = http://some.url/smokeping.cgi
...
#step = 300
#ping = 5You can use Vim to open the config file, or use SFTP to log in and open the config file with an editor. Here you need to modify the cgiurl and replace it with your IP or domain name. Please see the next section for detailed config.

Finally, give permissions to the password file:
chmod 600 /usr/local/smokeping/etc/smokeping_secrets.dist3. Install Apache and configure Smokeping
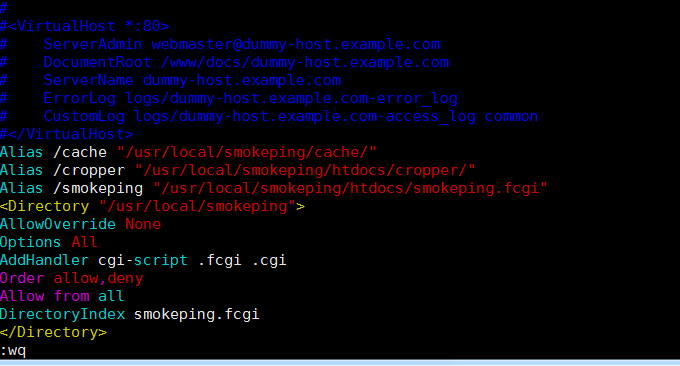
We have just installed Apache through the Yum method. Here we need to modify the Apache configuration file and adjust the IP or domain name to access the Smokeping path. The command is as follows:
vim /etc/httpd/conf/httpd.conf
#在最后添加以下内容
Alias /cache "/usr/local/smokeping/cache/"
Alias /cropper "/usr/local/smokeping/htdocs/cropper/"
Alias /smokeping "/usr/local/smokeping/htdocs/smokeping.fcgi"
<Directory "/usr/local/smokeping">
AllowOverride None
Options All
AddHandler cgi-script .fcgi .cgi
Order allow,deny
Allow from all
DirectoryIndex smokeping.fcgi
</Directory>
#######################################################
#如果你想让你的Smokeping访问不公开,你可以设置访问密码
vim /etc/httpd/conf/httpd.conf
Alias /cache "/usr/local/smokeping/cache/"
Alias /cropper "/usr/local/smokeping/htdocs/cropper/"
Alias /smokeping "/usr/local/smokeping/htdocs/smokeping.fcgi"
<Directory "/usr/local/smokeping">
AllowOverride None
Options All
AddHandler cgi-script .fcgi .cgi
AllowOverride AuthConfig
Order allow,deny
Allow from all
AuthName "Smokeping"
AuthType Basic
AuthUserFile /usr/local/smokeping/htdocs/htpasswd
Require valid-user
DirectoryIndex smokeping.fcgi
</Directory>
#再执行设置密码
htpasswd -c /usr/local/smokeping/htdocs/htpasswd adminYou can use the Vim command above, or you can use an editor to download the configuration file locally for editing.
Set up Smokeping and Apache to start at boot:
echo "/usr/local/smokeping/bin/smokeping --logfile=/var/log/smokeping.log 2>&1 &" >> /etc/rc.local
chkconfig httpd on4. Smokeping startup and problems encountered
Execute the following command to start Smokeping:
/etc/init.d/httpd start
/usr/local/smokeping/bin/smokeping --logfile=/var/log/smokeping.log2>&1&Open your browser and visit: ip or domain name/smokeping, and you can see the default interface of Smokeping.
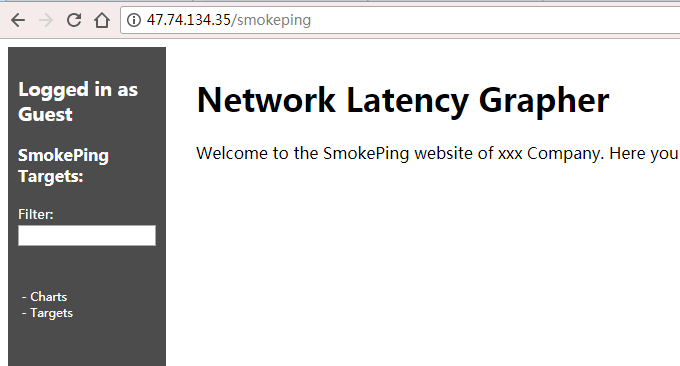
4.1 Smokeping supports Chinese issues
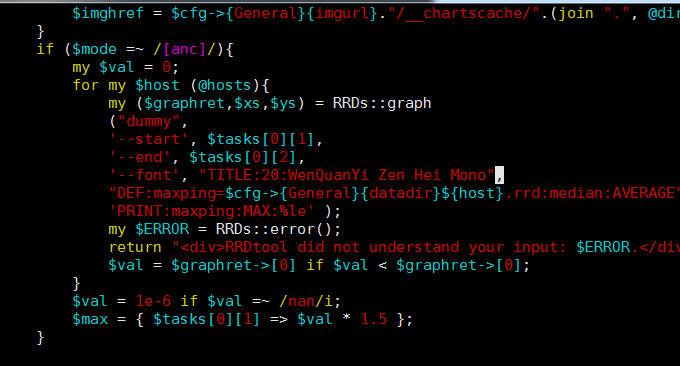
The default Smokeping display of Chinese characters will be garbled. We have just installed Chinese fonts for Linux on it. Now execute: vim /usr/local/smokeping/lib/Smokeping/Graphs.pm, in '- -end', $tasks[0][2],Add a line of font configuration part('--font', "TITLE:20:WenQuanYi Zen Hei Mono",), as follows:
...
if ($mode =~ /[anc]/){
my $val = 0;
for my $host (@hosts){
my ($graphret,$xs,$ys) = RRDs::graph
("dummy",
'--start', $tasks[0][1],
'--end', $tasks[0][2],
'--font', "TITLE:20:WenQuanYi Zen Hei Mono",
"DEF:maxping=$cfg->{General}{datadir}${host}.rrd:median:AVERAGE",
'PRINT:maxping:MAX:%le' );
my $ERROR = RRDs::error();
return "RRDtool did not understand your input: $ERROR." if $ERROR;
$val = $graphret->[0] if $val < $graphret->[0];
}
$val = 1e-6 if $val =~ /nan/i;
$max = { $tasks[0][1] => $val * 1.5 };
}
...Set as shown below:
Then, execute: vim /usr/local/smokeping/etc/config, add a line of code charset= utf-8, as follows:
...
***Presentation ***
charset= utf-8
template = /usr/local/smokeping/etc/basepage.html.dist
...4.2 Smokeping domain name access and SSL certificate
If you don’t want Smokeping to have a tail like /Smokeping when accessing it, you can modify it in the Apache configuration as follows:
Alias / "/usr/local/smokeping/htdocs/smokeping.fcgi" Adding an SSL certificate to a domain name is also very simple. First apply for an SSL certificate for your domain name. Alibaba Cloud, Tencent Cloud, etc. provide free one-year SSL certificates for application. For more free SSL certificates, please see here: Collection and summary of free SSL certificates - add HTTPS secure encrypted access to the website for free.
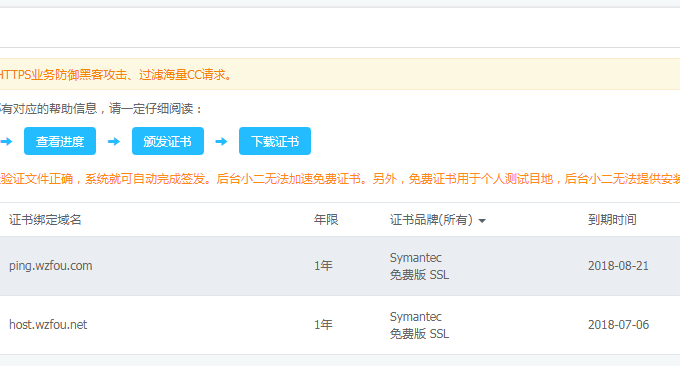
We have just installed mod_ssl through Yum. Now you can enter: /etc/httpd/conf.d, then replace your Key, CRT, and CA paths and find the following code (note your certificate path):
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
# the certificate is encrypted, then you will be prompted for a
# pass phrase. Note that a kill -HUP will prompt again. A new
# certificate can be generated using the genkey(1) command.
SSLCertificateFile /etc/pki/tls/certs/domain.crt
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
SSLCertificateKeyFile /etc/pki/tls/certs/domain.key
# Certificate Authority (CA):
# Set the CA certificate verification path where to find CA
# certificates for client authentication or alternatively one
# huge file containing all of them (file must be PEM encoded)
SSLCACertificateFile /etc/pki/tls/certs/domainca.crtPlease upload the CA root certificate, CRT domain name certificate and key you downloaded to the /etc/pki/tls/certs/ directory, and then replace the above three paths. Finally, restart Apache and you can see that the SSL certificate has taken effect.
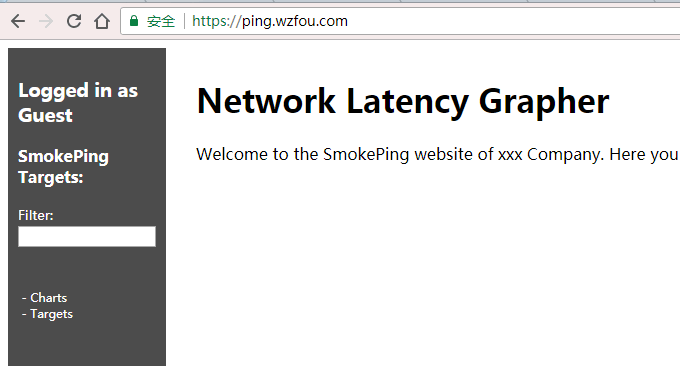
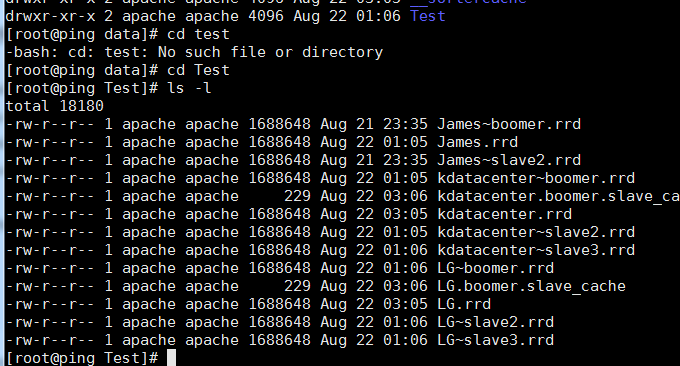
4.3 Smokeping does not display data problem
This problem is generally caused by directory permissions. You can check the Apache log error message and keep the attributes of the files generated in the three folders of cache data var as readable and writable and the owner is: apache:apache.
5. Detailed explanation of Smokeping template and Config configuration
Smokeping template file basepage.html.dist. In basepage.html.dist you can modify Smokeping's CSS style, add Html content (including images, text), modify title links, etc.

Detailed explanation of the Smokeping Config configuration file. The relevant Chinese description is as follows:
*** General *** ##全局配置
owner = charlie.cui@zerounix.com ##联系人(显示在网页上)
contact = charlie.cui@zerounix.com ##联系人邮箱
mailhost = mail.zerounix.com ##邮件服务主机
sendmail = /usr/sbin/sendmail ##发送邮件件的二进制可执行程序
# NOTE: do not put the Image Cache below cgi-bin
# since all files under cgi-bin will be executed ... this is not
# good for images.
imgcache = /usr/local/smokeping/cache ##生成图片的缓存
imgurl = cache ##cache 定义cgi程序显示图片的url目录
datadir = /usr/local/smokeping/data ##rrd文件的位置
piddir = /usr/local/smokeping/var
cgiurl = http://some.url/smokeping.cgi ##smokeping访问地址
smokemail = /usr/local/smokeping/etc/smokemail ##发送邮件的邮件内容模板
tmail = /usr/local/smokeping/etc/tmail ##HTML邮件模板的路径
# specify this to get syslog logging
syslogfacility = local0 ##syslog日志记录的设备编号
# each probe is now run in its own process
# disable this to revert to the old behaviour
# concurrentprobes = no
*** Alerts *** ##报警配置
to = monitor@zerounix.com
from = mon@zerounix.com
+网络中断
type = rtt
pattern = !=U,==U
comment = 网络中断
priority = 1
+中断恢复
type = rtt
pattern = ==U,!=U,!=U
comment = 中断恢复
priority = 2
+严重丢包
type = loss
pattern = >50%
comment = 丢包大于50%
priority = 3
+丢包报警
type = loss
pattern = >10%,>10%,>10%
comment = 连续3次丢包10%以上
priority = 4
+网络延迟
type = rtt
pattern = >180,>180,>180
comment = 连续3次延时180以上
priority = 5
*** Database ***
step = 60
pings = 10
# consfn mrhb steps total
AVERAGE 0.5 1 1008
AVERAGE 0.5 12 4320
MIN 0.5 12 4320
MAX 0.5 12 4320
AVERAGE 0.5 144 720
MAX 0.5 144 720
MIN 0.5 144 720
*** Presentation *** ##模板文件路径
template = /tmp/smokeping-31631-build/etc/basepage.html.dist
+ charts
menu = Charts
title = The most interesting destinations
++ stddev
sorter = StdDev(entries=>4)
title = Top Standard Deviation
menu = Std Deviation
format = Standard Deviation %f
++ max
sorter = Max(entries=>5)
title = Top Max Roundtrip Time
menu = by Max
format = Max Roundtrip Time %f seconds
++ loss
sorter = Loss(entries=>5)
title = Top Packet Loss
menu = Loss
format = Packets Lost %f
++ median
sorter = Median(entries=>5)
title = Top Median Roundtrip Time
menu = by Median
format = Median RTT %f seconds
+ overview
width = 600
height = 50
range = 10h
+ detail
width = 600
height = 200
unison_tolerance = 2
"Last 3 Hours" 3h
"Last 30 Hours" 30h
"Last 10 Days" 10d
"Last 400 Days" 400d
#+ hierarchies
#++ owner
#title = Host Owner
#++ location
#title = Location
*** Probes *** ##探针
+ FPing
binary = /usr/local/sbin/fping
+ DNS
binary = /usr/bin/dig
lookup = name.example
*** Slaves *** ##“从”服务器设置
secrets=/usr/local/smokeping/etc/smokeping_secrets
+boomer
display_name=boomer
color=0000ff
+slave2
display_name=another
color=00ff00
*** Targets *** ##监控目标
probe = FPing
menu = Top
title = Network Latency Grapher
remark = Welcome to the SmokePing website of xxx Company.
Here you will learn all about the latency of our network.
+ Test
menu= Targets
#parents = owner:/Test/James location:/
++ James
menu = James
title =James
alerts = someloss
slaves = boomer slave2
host = james.address
++ MultiHost
menu = Multihost
title = James and James as seen from Boomer
host = /Test/James /Test/James~boomerAdd monitoring target . *** Targets *** The monitoring host has a hierarchical structure, represented by +, for example, "+" on the first layer, "++" on the second layer, and so on. Here is a sample code for pinging from local to three major networks and returning data:
+ Other
menu = 三大网络监控
title = 监控统计
++ dianxin
menu = 电信网络监控
title = 电信网络监控列表
host = /Other/dianxin/dianxin-bj /Other/dianxin/dianxin-hlj /Other/dianxin/dianxin-tj /Other/dianxin/dianxin-sc /Other/dianxin/dianxin-sh /Other/dianxin/dianxin-gz
+++ dianxin-bj
menu = 北京电信
title = 北京电信
alerts = someloss
host = 202.96.199.133
+++ dianxin-hlj
menu = 黑龙江电信
title = 黑龙江电信
alerts = someloss
host = 219.147.198.242
+++ dianxin-tj
menu = 天津电信
title = 天津电信
alerts = someloss
host = 219.150.32.132
+++ dianxin-sc
menu = 四川电信
title = 四川电信
alerts = someloss
host = 61.139.2.69
+++ dianxin-sh
menu = 上海电信
title = 上海电信
alerts = someloss
host = 116.228.111.118
+++ dianxin-gz
menu = 广东电信
title = 广东电信
alerts = someloss
host = 113.111.211.22
++ liantong
menu = 联通网络监控
title = 联通网络监控列表
host = /Other/liantong/liantong-bj /Other/liantong/liantong-hlj /Other/liantong/liantong-tj /Other/liantong/liantong-sc /Other/liantong/liantong-sh /Other/liantong/liantong-gz
+++ liantong-bj
menu = 北京联通
title = 北京联通
alerts = someloss
host = 61.135.169.121
+++ liantong-hlj
menu = 黑龙江联通
title = 黑龙江联通
alerts = someloss
host = 202.97.224.69
+++ liantong-tj
menu = 天津联通
title = 天津联通
alerts = someloss
host = 202.99.96.68
+++ liantong-sc
menu = 四川联通
title = 四川联通
alerts = someloss
host = 119.6.6.6
+++ liantong-sh
menu = 上海联通
title = 上海联通
alerts = someloss
host = 210.22.84.3
+++ liantong-gz
menu = 广东联通
title = 广东联通
alerts = someloss
host = 221.5.88.88
++ yidong
menu = 移动网络监控
title = 移动网络监控列表
host = /Other/yidong/yidong-bj /Other/yidong/yidong-hlj /Other/yidong/yidong-tj /Other/yidong/yidong-sc /Other/yidong/yidong-sh /Other/yidong/yidong-gz
+++ yidong-bj
menu = 北京移动
title = 北京移动
alerts = someloss
host = 221.130.33.52
+++ yidong-hlj
menu = 黑龙江移动
title = 黑龙江移动
alerts = someloss
host = 211.137.241.35
+++ yidong-tj
menu = 天津移动
title = 天津移动
alerts = someloss
host = 211.137.160.5
+++ yidong-sc
menu = 四川移动
title = 四川移动
alerts = someloss
host = 218.201.4.3
+++ yidong-sh
menu = 上海移动
title = 上海移动
alerts = someloss
host = 117.131.19.23
+++ yidong-gz
menu = 广东移动
title = 广东移动
alerts = someloss
host = 211.136.192.66. Smokeping master-slave server distributed deployment
Above we saw in the configuration file: *** Slaves ***, which is used to deploy the master-slave server. described as follows:
*** Slaves ***
secrets=/usr/local/smokeping/etc/smokeping_secrets.dist
# 定义通信用的秘钥文件,里面包含slave的名字以及对应密码
+ wzfou # slave的名字
display_name=挖站否 # slave的别名
location=杭州电信机房 # 这个字段用来定义slave主机的位置,类似于description
color=0000ff # slave收集的数据在图像中显示的颜色6.1 Smokeping master server settings
First deploy the main server Smokeping according to the above method, and then modify the contents of smokeping_secrets.dist. Set the Slave name and password as shown below:
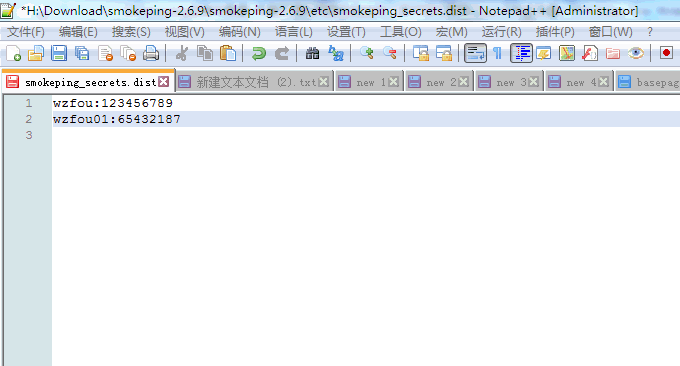
The content of the secret key file used for communication is "slave name: password". You need to pay attention to the permissions of the key file here. Since smokeping's master/slave is verified through the smokeping program, the owner of this key file must be The user identity of the smokeping process is running, and the permissions are 600. The command is as follows:
chown apache:apache /usr/local/smokeping/etc/smokeping_secrets.distchmod 600 /usr/local/smokeping/etc/smokeping_secrets.dist
Next, assign the defined Slave node to the host you need to monitor, as follows:
*** Targets ***
++ changzhou ## 一级菜单,这个值将会作为data下的一个目录名被创建
menu = 常州机房 ## 定义web上显示的菜单名
title = 常州机房 ## 标题名称
+++ dianxin ## 监控主机,数据将会被存放在 data/changzhou/dianxin目录下
menu = 电信机房 ## web上显示的名称
title = 电信机房监控 ##网页标题
alerts = someloss ## 报警
slaves = wzfou ## slave节点
host = wzfou.com ## 被监控的主机IP或者域名 From the above configuration, we can see that the key point is to add a line in *** Targets ***: slaves = wzfou ## slave node, indicating that slaves will monitor this target like the master server .
6.2 Smokeping slave server settings
Please follow the above method to configure Smokeping in the slave server. No configuration is required, and there is no need to modify the Apache configuration. Just ensure that Smokeping is installed and running normally. There are several parameters you need to understand when starting the slave server with Smokeping:
–master-url: When smokeping is running in slave mode, use this item to specify the access url of the master (web interface, used for communication)
–slave-name: By default, when this item is not specified, after the slave connects to the master, the master will use the slave’s hostname as the slavename. If you do not want to do this, you need to manually specify the change option.
–shared-secret: Password file for communication authentication with master
–cache-dir: When smokeping is running in slave mode, the directory path where temporary data is stored on the master
–pid-dir: In slave mode, the directory path where its pid is stored. Optional parameter, inherits the value of the –cache-dir parameter by default
Similarly, make sure that the owner of the smokeping_secrets.dist file of your Smokeping slave server is the user running the smokeping process, and the permissions are 600, and only needs to write the password in the smokeping_secrets.dist of the slave server, which is different from the master server.
This is my Smokeping command example to start from the server (note that the name of the slave is replaced):
/usr/local/smokeping/bin/smokeping --master-url=https://ping.wzfou.com/ --cache-dir=/usr/local/smokeping/cache/ --shared-secret=/usr/local/smokeping/etc/smokeping_secrets.dist --slave-name=wzfou --logfile=/var/log/smokeping_slave.logCopy
7. Summary
Smokeping is really a very powerful network performance monitoring tool. The effect can be viewed at: ping.wzfou.com. Smokeping also has many probes available for use, such as Ping, DNS, Curl, HTTPS, SMTP, FTP, TCP, LDAP, etc. There are even many plug-ins that you can install and develop yourself. (Click to enlarge)
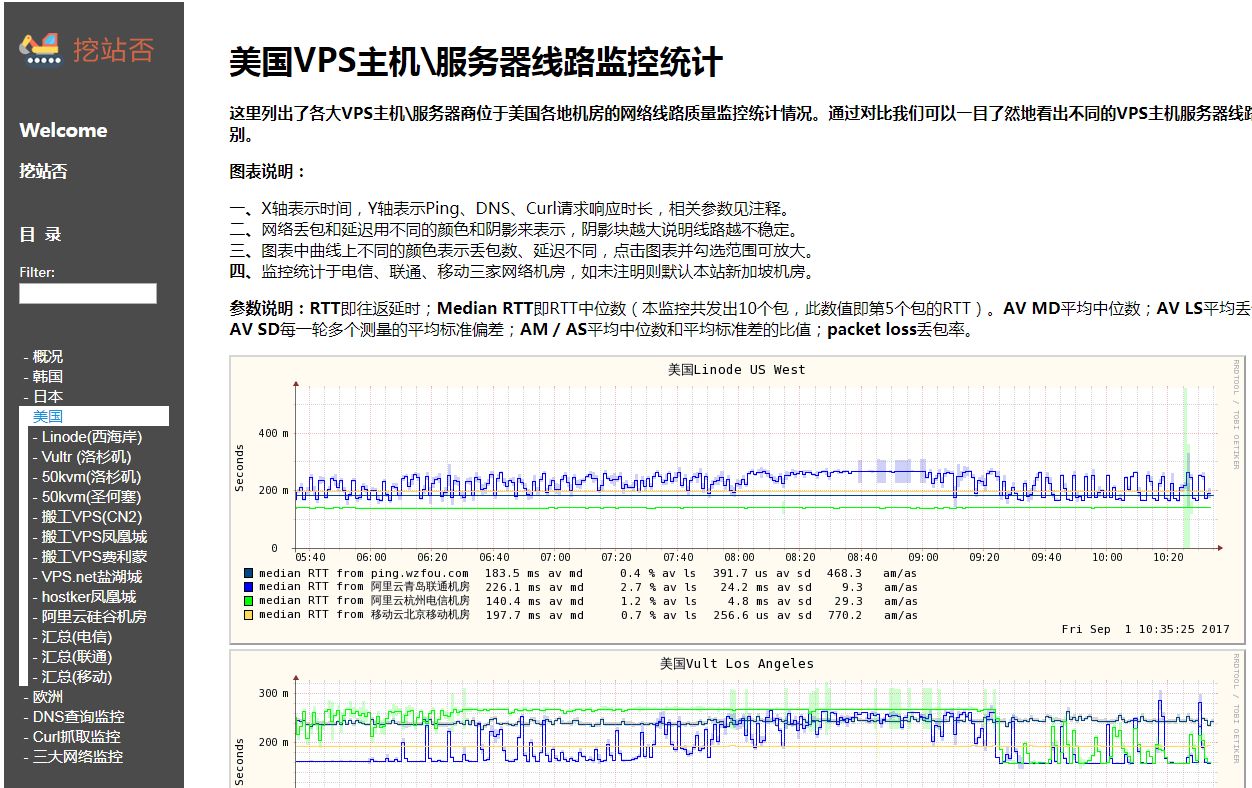
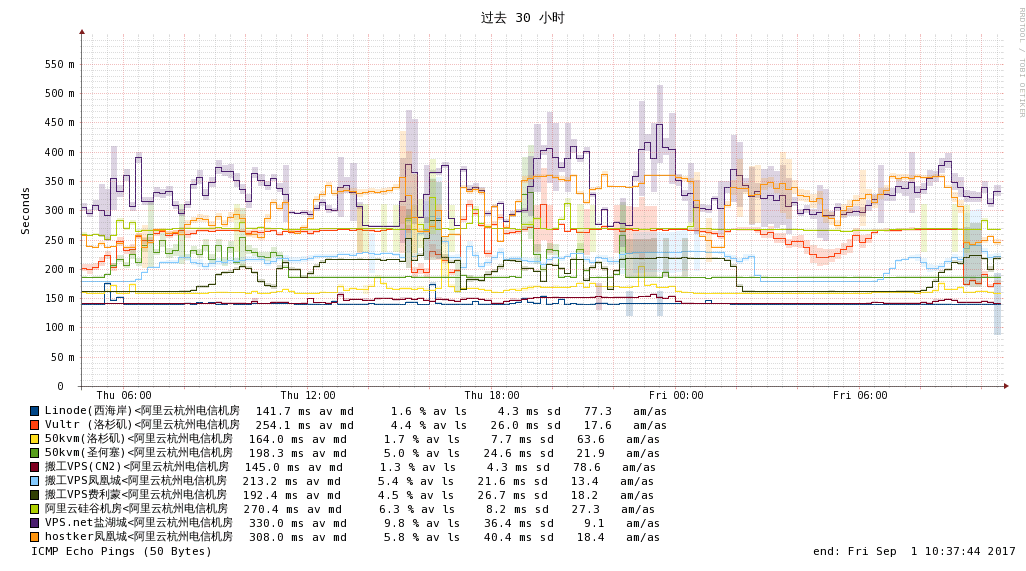
This is Smokeping's chart, which is very intuitive and easy to understand. (Click to enlarge)
File permissions issue. This is a place where problems can easily occur. After modifying the config file, data will be generated in the datacachevar. If the file permissions are not apache, it will directly cause the rrd file not to be updated, the web page has no image, or the web page has an image but does not. data.
You can solve the problem by executing the following command on the server:
pkill smokeping
chown -R apache:apache /usr/local/smokeping/data
chown -R apache:apache /usr/local/smokeping/cache
/etc/init.d/httpd restart ##重启Apache
/usr/local/smokeping/bin/smokeping --reload Restart smokeping. You need to restart the smokeping process every time you modify the configuration file, otherwise various problems will occur. The command to restart smokeping is as follows:
/usr/local/smokeping/bin/smokeping --restartor
/usr/local/smokeping/bin/smokeping --reloador
pkill smokeping
/usr/local/smokeping/bin/smokepingThe master/slave server has no data. For the master/slave architecture, first ensure that the slave-name corresponds to the slave node name configured in the master configuration file and the node name in the key file. Then check whether the master's key file (including the slave node name and password) corresponds to the slave's password file (only the password). Finally, the key attribute permissions must be 600.
PS: Updated on November 11, 2017, Smokeping is excellent at server network monitoring, but if you want to monitor the memory, CPU, connection and other indicators of the entire server in detail, you can try the enterprise level Zabbix: Zabbix installation and use - a powerful server performance monitoring tool to control server software and hardware resources.
