Recently, when a friend was using his Yunfu host, he discovered that SSH has been violently scanned by others. Although the SSH account and password have never been guessed, if someone keeps staring at him, something will happen sooner or later. I helped him set up an S-S-H login whitelist, which only allows login access from his own IP, and rejects all other IPs.
In fact, the easiest way to ensure that S-S-H is not cracked is to modify the default port 22. For example, the classic VPS we use has port 22 modified by default when the VPS is created. The most thorough method is to prohibit the use of account and password to log in, and instead use a key to log in. As long as the key is kept safe, no one can enter the server.
This article will share some basic methods for Linux VPS host and server security protection, such as modifying the SSH port; adding a whitelist to SSH login to only allow access from your own IP; you can also set up a key login to prohibit password login. In this way, the cracker will have "no way in".
Of course, experienced friends can also directly turn off S-S-H login. If a panel such as Pagoda BT panel WDCP has been installed, you can directly choose to turn off S-S-H in the background of the panel, or turn them off manually. Some merchants such as Alibaba Cloud, Tencent Cloud, etc. also have their own security groups. You can also choose to temporarily block ports such as 22 in the security group, and then manually open the ports when you need to use them. Although it is a bit troublesome, it is relatively easy. Simple and convenient method.

For more tutorials on server security and website building, here are:
- Improve website search - Baidu, Google custom search and Elasticsearch self-built search
- Ten CloudFlare Free CDN Acceleration Tips You May Not Know-SSLDDOSCache
- How to enable Nginx fastcgi_cache cache acceleration in WordPress - Nginx configuration example
PS: Updated on March 19, 2020 , if your website has been hacked, you can refer to the following methods to solve the problem: Website Trojans and server hacking troubleshooting analysis - VPS host and server security methods.
1. Modify the default port
The default port is 22, which is easy to be cracked. We can change the port number to another one. Order:
#SSH服务的启动与停止 service sshd status # 状态 service sshd start # 启动 service sshd stop # 暂停 service sshd restart # 重启 #改完端口后记得在防火墙放行,例如 iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 8080 -j ACCEPT #保存防火墙规则并重启 /etc/init.d/iptables save service iptables restart #修改端口号 #主配置文件:/etc/ssh/sshd_config Port 22

5.1 Generate public and private keys
The easiest way is to use the command directly on the Linux VPS host to quickly generate:
# 生成 SSH 密钥对 [root@wzfoume ~]# ssh-keygen -t rsa Generating public/private rsa key pair. # 建议直接回车使用默认路径 Enter file in which to save the key (/root/.ssh/id_rsa): # 输入密码短语(留空则直接回车) Enter passphrase (empty for no passphrase): # 重复密码短语 Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: e3:62:aa:0f:28:87:8f:2e:dd:fb:f0:59:fb:24:07:4a root@wzfoume The key's randomart image is: +--[ RSA 2048]----+ | | | | | | | | | E S | | o . o o | |+.o.. + + o | |o+...= + = | |+.oo+o+ ... | +-----------------+ [root@wzfoume ~]#
The generated key can be found under the .ssh file under root.

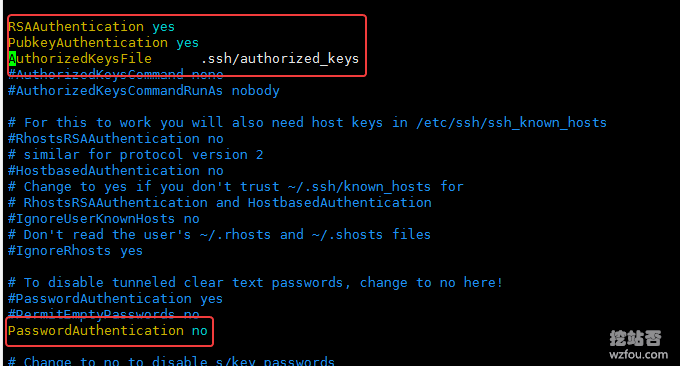
The configuration modification is as shown below:

5.3 Disable password login
Now you can choose to use a key when connecting using Xshell or Putty.

When you confirm that there is no problem with the key connection, you can disable password login and only key login is available. The method is: modify the /etc/ssh/sshd_config file and change PasswordAuthentication yes to PasswordAuthentication no; finally, restart sshd.

6. Summary
We must pay enough attention to the issue of S-S-H security. The simplest operation is to set a more complex password and modify the default S-S-H port. This operation can prevent a large part of brute force scanning.
Choosing to turn off S-S-H will also cause inconvenience to yourself. A safer way is to disable password login and use key login instead. At the same time, the public key and the private key are stored separately, so they can be easily seen through if leaked.
