DNSSEC is a security mechanism designed to solve DNS spoofing and cache pollution. The English name is Domain Name System Security Extensions. It uses cryptographic technology to enable the domain name resolution server to verify the responses it receives (including responses for non-existent domain names). ) came from a real server, or was tampered with during transmission.
Simply put, DNSSEC can prevent DNS hijacking and ensure that the domain name requested by the user during the DNS resolution process is consistent with the corresponding IP address. Previously, a friend of mine in JD Cloud DNS free domain name resolution suggested using DNSSEC+CAA in combination, which can ensure the security of DNS resolution to the greatest extent. This article uses Google Cloud DNS to set up DNSSEC as a demonstration.
Enabling DNSSEC requires the joint efforts of domain name registrars, DNS domain name resolvers, and local DNS to support DNSSEC technology. Domestic domain name registrars such as Alibaba Cloud, Tencent Cloud, and Baidu Cloud do not yet know whether they support DNSSEC. From the common foreign domain name registrars I use such as GodaddyNameNameCheapNamesilo, they all support DNSSEC.
In order to make domain name DNS resolution more accurate, the safest way is to enable HSTS+DNS CAA and DNSSEC+DNS over HTTPS or DNS-Crypt on the browser client. Currently, wzfou.com has adopted Https, CAA, HSTS, and DNSSEC. and other technologies, relevant tutorials include:
- Collection and summary of free SSL certificates - add HTTPS secure encrypted access to the website for free
- Enable HSTS and join the HSTS Preload List to make HTTPS access to the website more secure - with a method to delete HSTS
- JD Cloud DNS free domain name resolution - supports regional segmentation of lines and can add CAA resolution records
PS: Updated on July 22, 2018, Although Google Cloud DNS supports DNSSEC, it does not support secondary/backup DNS. Friends who need Secondary DNS can try: He.net DNS domain name resolution application- Free DDNS, IPv6 address and Slave DNS.
1. Which DNS domain name resolution services support DNSSEC?
Domestic DNS shield (dnsdun.com) seems to be the only DNS resolution service provider currently supporting CAA and DNSSEC resolution records. Others such as DNSPOD, Alibaba Cloud DNS, Cloudxns, etc. do not support DNSSEC. However, the DNS shield is too niche. Although I have known about it for several years, its stability still needs to be considered.

There are only a handful of foreign DNS domain name resolutions that support DNSSEC. Currently, only Cloudflare, Google Cloud DNS, and Rage4 support DNSSEC. In addition, Cloudflare does not support setting up DNSSEC-specific records, such as IPSECKEY, SSHFP, TLSA, DNSKEY, DS records. It is recommended to use Google Cloud DNS and Rage4.

2. How popular is DNSSEC? domestic?
- HTTPS://stats.labs.APN IC.net/
The following is the popularity of DNSSEC in different places around the world on stats.labs.apnic.net. It can be seen from the chart that there are still quite few DNS servers supporting DNSSEC in the world, with the total number not exceeding 15%. The situation in China is even worse, below 1%. (Click to enlarge)

3. Google Cloud DNS Price and Usage Tutorial
- HTTPS://cloud.Google.com/DNS/
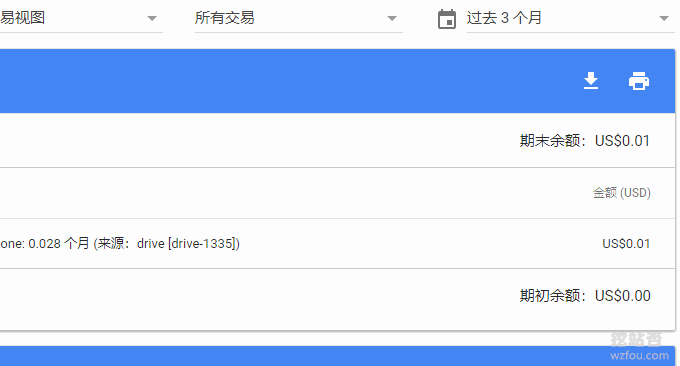
Both Google Cloud DNS and Rage4 support the use of DNSSEC, but Rage4 starts at €2/month per domain name and is priced based on functions rather than usage, while Google Cloud DNS starts at $0.2/month per domain name , $0.4/million requests. So wzfou.com chose Google Cloud DNS.
The detailed usage of Google Cloud DNS has been shared before giving up free DNS and switching to paid DNS-Google cloud DNS application and resolution effects. Here is a brief introduction to the usage of Google Cloud DNS. The first is to log in to the Google Cloud platform and find the DNS resolution.
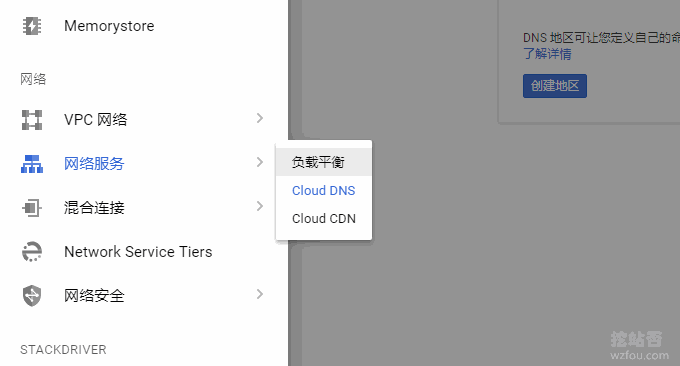
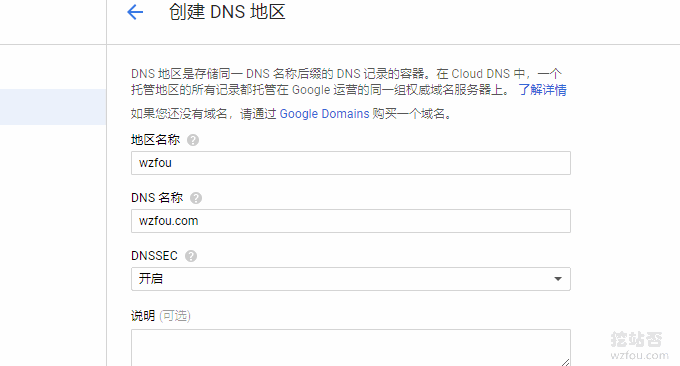
Then click Create DNS Name.
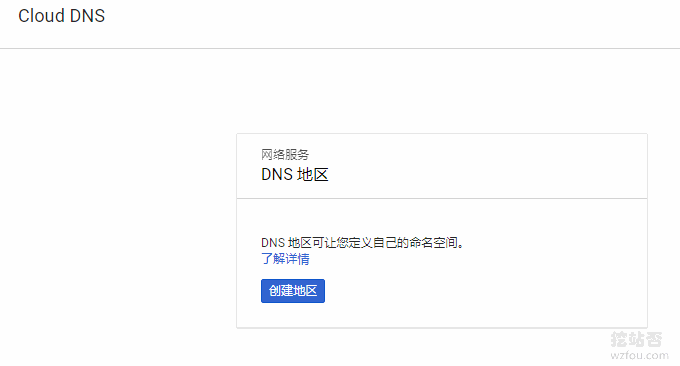
You can choose any region name as long as it doesn't repeat. The DNS name is the domain name you want to resolve, such as wzfou.com. If you want to enable DNSSEC, select Enable. Sure.
It is relatively simple to add a DNS resolution record to Google Cloud DNS. If it is a record like @, just leave it blank, as shown below:

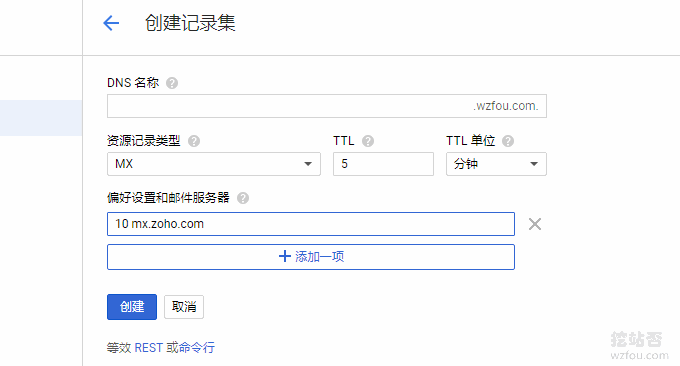
Google Cloud DNS supports A, AAAA, CNAME, NS, MX, TXT, SRV, SPF, LOC, NAPTR, PTR, CAA and DNSSEC related records. Currently it is the most complete.

It should be noted that Google Cloud DNS adds DNS records in the form of sets. For example, if MX has two records, you only need to click to add another one.
Google Cloud DNS adds CAA records as shown in the figure below. For methods to generate CAA records, please refer to: JD Cloud DNS settings CAA.

4. Domain name registrar Name enables DNSSEC
Find "Registrar Settings" in Google Cloud DNS.

Then click to display the NS server and DS record of Google Cloud DNS.
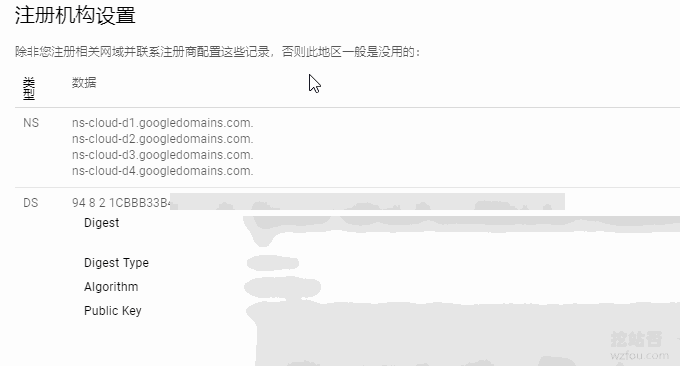
Go to the domain name registrar Name (PS: The method is similar to other domain name registrars you use) and modify the NS server to Google Cloud DNS.
ns-cloud-d1.googledomains.com
ns-cloud-d2.googledomains.com
ns-cloud-d3.googledomains.com
ns-cloud-d4.googledomains.com
As shown below:

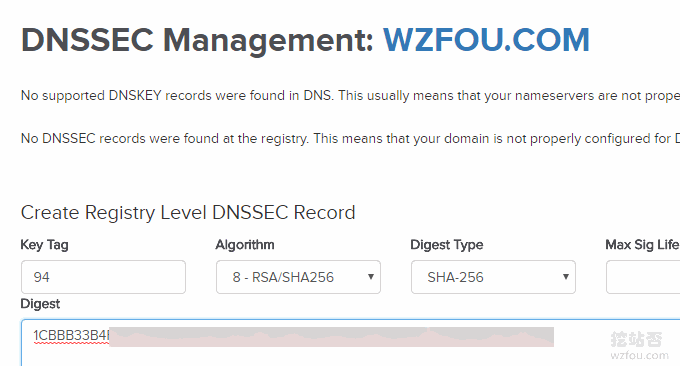
Then fill in the DS record in the DNSSEC management interface of Name, mainly Key Tag, Algorithm, Digest Type and Digest.
5. Check whether DNSSEC is successfully enabled and its effect
- HTTPS://DNS Sec-analyzer.VE Day Cream IGN labs.com/
Go to the verisignlabs website and enter your domain name. If your DS is configured correctly, you will see a green "hook".

Use webmaster tools to test wzfou.com with Google Cloud DNS enabled, and there are no problems with the connection anywhere.

When using the search engine crawling test of Baidu Webmaster Platform, all the results indicate that the crawling is successful, indicating that Google Cloud DNS is running normally in China.

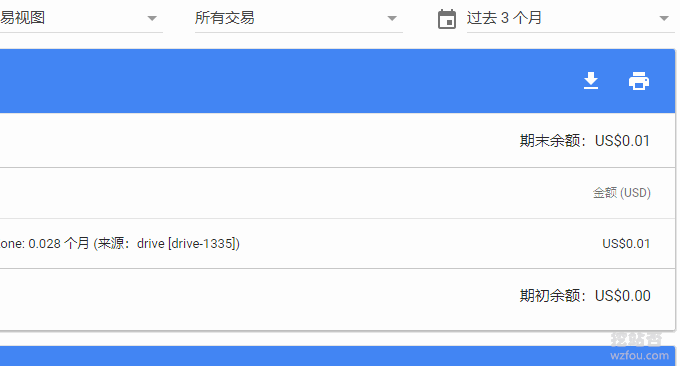
In addition, Google Cloud DNS charges are really quite cheap.
6. Summary
Theoretically speaking, enabling DNSSEC and CAA can basically prevent DNS hijacking. However, since the current penetration rate of DNSSEC is very low, especially domestic DNS basically does not support DNSSEC, the effect of using DNSSEC in China may not be good. But "better than nothing", after all, DNSSEC is a major development trend.
The first group of the four sets of NS servers of Google Cloud DNS cannot be pinged in China, but from the monitoring point of view, DNS does not affect it. In addition, it should be noted that it is useless to use DNSSEC for already contaminated domain names. Instead, you can use DNS over HTTPS or DNS-Crypt to encrypt the entire DNS resolution process.
