More and more people are using VPS hosts to build websites, but compared with virtual hosts or managed servers, personal VPS hosts are basically unmanaged. That is, the host provider is only responsible for the smooth network of the VPS host. As for technical issues You have to figure it out on your own. In the past, the VPS hosts used by Alibaba Cloud were often attacked by CC and DDOS. Basically, every time they were attacked, they would enter Alibaba Cloud's "black hole".
Alibaba Cloud's VPS hosts for CC and DDOS generally cannot defend against too much traffic. Once the attack traffic increases, the routes will basically be cleared. If there are too many attacks, there will even be a "black hole" for one or several days. Now I have moved my website to the classic CN2 VPS porter. I have received reminders from enthusiastic friends before that the porter only treats CC and DDOS three times. If it exceeds three times, it will directly block the VPS.
This attack also taught me that I still need to be cautious when placing my website on a classic VPS host. I couldn't open the site at the beginning, and then I was reminded by messages from many friends. I immediately logged in to the hosting provider's backend to check. From the monitoring chart, I can see that the CPU usage of the VPS exceeded 100%, and the bandwidth speed exceeded hundreds. MB, apparently the VPS was disconnected by the hosting provider.
This article will share with friends who use VPS hosts to build websites, the basic steps to deal with small CC and DDOS attacks, which basically revolve around blocking malicious IPs through firewalls.

For more website security and experience in website construction, there are:
- Five security tips for using a free VPS control panel – don’t let hackers take advantage
- Linux php-fpm optimization experience-php-fpm process takes up large memory and does not release memory problems
- DNS domain name resolution enables DNSSEC to prevent DNS hijacking-Google Cloud DNS settings DNSSEC
PS: Updated on March 6, 2018, If you want to prevent specific IPs from accessing the website, you can use this method: Website blocking and blocking IP access settings for specific regions and countries - PHP code/Nginx/ WordPress settings.
PS: Updated on March 19, 2020 , if your website has been hacked, you can refer to the following methods to solve the problem: Website Trojans and server hacking troubleshooting analysis - VPS host and server security methods.
1. Do your homework in advance when dealing with CC and DDOS
You can quickly judge the current attack with the following two commands: Enter the following command to view the number of connections for a single IP.
netstat -nat|grep -i '80'|wc -l
Sort the connected IPs by the number of connections and view the TCP connection status.
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
1.1 Frequent backup-combination of local and off-site backup
Website backup is a surefire way to deal with CC and DDOS attacks. Regardless of the attack, as long as the data is not destroyed, we can minimize the loss. For frequently updated data, it is recommended to back up once a day. Some hosting providers will also provide snapshot backup functions, such as Alibaba Cloud, Tencent Cloud, and the Linode snapshot introduced previously.

In addition to local backup, it is natural to do off-site backup. Off-site backup can be combined with cloud storage or cloud disk to save data. The Linux VPS shared earlier can automatically upload the data on the VPS to the network disk by mounting Google Drive and Dropbox, or use DigitalOcean Spaces cloud storage or cloud shooting. , Qiniu Cloud Storage, Baidu BOS and other professional cloud storage.
1.2 Learn to check the Linux VPS system load
Once we suffer CC and DDOS attacks, we can usually check it through the control panel of the VPS hosting provider. We can see obvious "abnormalities" in our monitoring data. The picture below shows 100% IO, CPU, memory, etc. displayed by the VPS host monitoring when I was attacked. (Click to enlarge)

2.2 Use Fail2ban to block attacking IPs
fail2ban is a monitoring software developed in Python language. It calls iptables to block the corresponding login IP by monitoring the login information of the system log to prevent malicious access by a certain IP. fail2ban reads the corresponding log file, Debian/Ubuntu:/var/log/auth.log, CentOS/Redhat:/var/log/secure. Install fail2ban:
apt-get install fail2ban
#CentOS内置源并未包含fail2ban,需要先安装epel源
yum -y install epel-release
#安装fial2ban
yum -y install fail2banAfter the installation is complete, the main configuration files are in the /etc/fail2ban directory, which contains two files and two directories:
fail2ban.conf: The configuration file defines the log level, log file location and socket recorded by fail2ban.
jail.conf defines those services to be monitored and some strategies used.
The beginning of jail.conf is the default global configuration block [DEFAULT]. The default configuration is described as follows:
[DEFAULT]
#忽略哪些IP,可以是具体IP、CIDR类型的地址,多个IP用空格分开
ignoreip = 127.0.0.1
#设置IP被锁住的时间,单位为秒
bantime = 600
#检测时间,在此时间内超过规定的次数会激活fail2ban
findtime = 600
#尝试的次数
maxretry = 3
#日志检测机器,有"gamin", "polling" and "auto"三种模式。
backend = polling
#发送报警邮件的地址
destemail = root@localhost #默认的动作执行行为,在action.d目录下有各种行为策略,默认是iptables-#multiport
banaction = iptables-multiport
#0.8.1版本后fail2ban默认用sendmail MTA
mta = sendmail
#默认使用tcp协议
protocol = tcp
#定义了各种行动的参数
#banaction参数在action.d目录下具体定义,name port protocol 也可以自己定义
#只禁止IP
action_ = %(banaction)s[name=%(__name__)s, port="%(port)s", protocol="%(protocol)s]
#即禁止IP又发送email
action_mw = %(banaction)s[name=%(__name__)s, port="%(port)s", protocol="%(protocol)s]
%(mta)s-whois[name=%(__name__)s, dest="%(destemail)s", protocol="%(protocol)s]
#禁止IP、发送email、报告有关日志
action_mwl = %(banaction)s[name=%(__name__)s, port="%(port)s", protocol="%(protocol)s]
%(mta)s-whois-lines[name=%(__name__)s, dest="%(destemail)s", logpath=%(logpath)s]
#如果没有定义行为,则默认的行为为action,可选择action_,action_mw, action_mwl 等
action = %(action_)s
默认配置文件含有此模块
#定义子模块名
[ssh]
#是否激活
enabled = true
#定义port,可以是数字端口号表示,也可以是字符串表示
port= ssh
#过滤规则,在filter.d目录下定义
filter = sshd
#检测日志的路径
logpath = /var/log/auth.log
#尝试的次数,覆盖了全局配置的
maxretry = 6
#banaction 在action.d目录下定义,此参数值会替换action中选用的默认行为中定义的banaction参数
banaction = iptables-allports
#注意 port protocol banaction 可以不用分开定义,直接使用action定义也可以,例如:
#action = iptables[name=SSH, port=ssh, protocol=tcp]
#在子模块中定义的port protocol banaction 都会在action_ action_mw, action_mwl中替换成具体的设置值。Fail2ban’s other directory functions are described as follows:
The filter.d directory defines rules for filtering based on log files, mainly using regular expressions to match keywords that cause errors.
The action.d directory contains what kind of actions should be taken against the corresponding IP according to the filtering rules.
Fail2ban anti-CC attack example:
#需要先新建一个nginx日志匹配规则
vi /etc/fail2ban/filter.d/nginx-cc.conf
#填写如下内容
[Definition]
failregex = <HOST> -.*- .*HTTP/1.* .* .*$
ignoreregex =
Continue to modify jail.local and add the following content:
[nginx-cc]
enabled = true
port = http,https
filter = nginx-cc
action = %(action_mwl)s
maxretry = 60
findtime = 60
bantime = 3600
logpath = /data/wwwlogs/wzfou.com_nginx.log
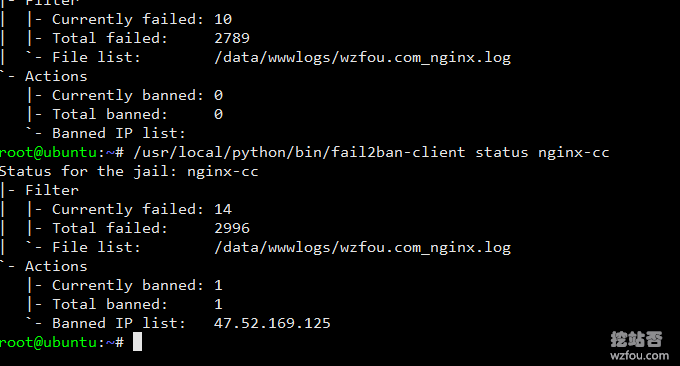
The above configuration means that if the same IP reaches 60 requests within 60 seconds, its IP will be banned for 1 hour. Remember to modify your website log path. Use the following command to view the fail2ban status and display the list of banned IP addresses.
/usr/local/python/bin/fail2ban-client status ssh-iptables
After saving the above code, grant x (execution) permission. To realize that the Shell Script is similar to a daemon in the background, you need to use nohup:
nohup 该shell script的位置 >/dev/null 2>&1 &>/dev/null 2>&1 means to redirect the information output by executing the shell script (several echoes in the shell script, used for debugging) to /dev/null. The & at the end represents background execution. In this case, even if you log out, the Shell Script will still be executed in the background.
3. Summary
I have used the above two scripts that detect website logs in real time and automatically add abnormal IPs to iptables for blocking. The results are very good and are enough to deal with small CC attacks. Currently, Fail2ban is used to detect website logs and block malicious IPs. Each of the three scripts has its own advantages, and you can choose according to your own needs.
However, if you encounter a larger DDOS attack, you still have to use a specialized anti-attack service. For example, Cloudflare anti-attack service is very effective. Basically, everyone in the VPS industry uses it. If your website has been attacked and becomes inaccessible, you can upgrade Cloudflare to the paid version, which will provide better protection.
